I stay back in the office during night and return back at around 6-7 am, when everybody is coming :). These nights are supposed to be LONELY as I am the only one in the building (actually in all the four buildings combined), apart from the security guards and office boys, of course. However, I’ve found my companions, and ways to refresh myself. I’ll list some of them.
1. Online Web/Security Cameras: Some of you who know that Google provides an API for refining the search queries (with a capital “R”) also know that the giant’s database is like an ocean. And you never really know what’s inside an ocean unless and until you dive in it. As you dive deeper, your jaw drops in awe.
Long story cut short, I use the query to discover (a part of) all AXIS cameras online.
For curious lot, the query is: inurl:/view/view.shtml AXIS and sometimes intitle:”Live View / – AXIS” | inurl:view/view.sht
[As I am writing this, I wanted check the second query. So I chose one of the results and something spooky happened. Someone was already controlling the camera. hehe.
I was moving it right, he/she was moving it left. We fought for a while but then I closed the window. I am nice guy you see :D)
Okay let’s proceed.
So I have a bookmarked folder called “PastTime” on my browser, which has my favorite cameras bookmarked. My most fave are:
i) A coffee/wine shop camera, which is more lively during the night. Luckily, the camera is provided officially, so I can provide the link without any worries. Find the link to the camera here: buzzjunction_webcam

ii) A camera in the study room of a Polytechnic school of NewYork. It’s a small room with a coffee machine, a microwave oven (?), a printer, a sofa, a bookshelf, and an elliptical table with power connection for the laptops and notebooks.
And that’s the best part. People come here with there laptops, and sometimes I sit down looking at there screens, trying to figure out what they are doing. 😛
I have also become acquainted with some regular visitors.
A spectacled guy with a cap and a laptop. (He is leaving right now. No kidding. What a coincidence [jawdrop])
A black girl, who has the headphones exactly like mine.
Two Muslim girls, with one Dell XPS laptop (probably).
The bad part is, there are no visitors on sundays 🙁
iii) A micro/nano lab camera of one of the world’s most famous universities. There’s nothing engaging about this, apart from the fact that the guys (or girls) roam around in spacesuit sort of dresses.
iv) A set of four surveillance cameras. Three of them pointing to car parking locations and one focussed inside some kind of room. I am still not able to get it yet. The only thing that makes me stick to it is the word “surveillance” 😀
There are couple of others focussed on traffic, colleges, hostels (I guess), lake, parks… but they are pretty boring and pictures are not really clear.
I’d like to try my hands on other cameras like linksys too. Let’s see when.
2. Google Again: Google queries can be real fun.
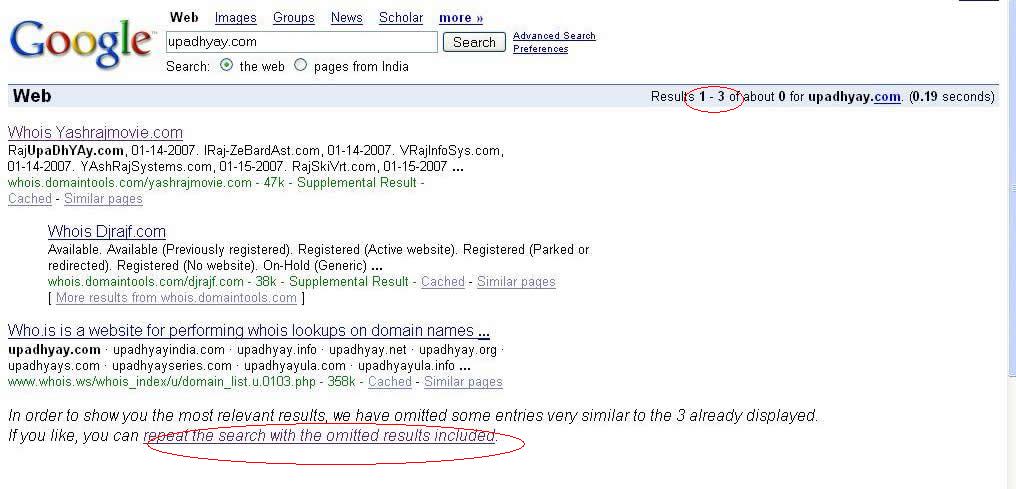
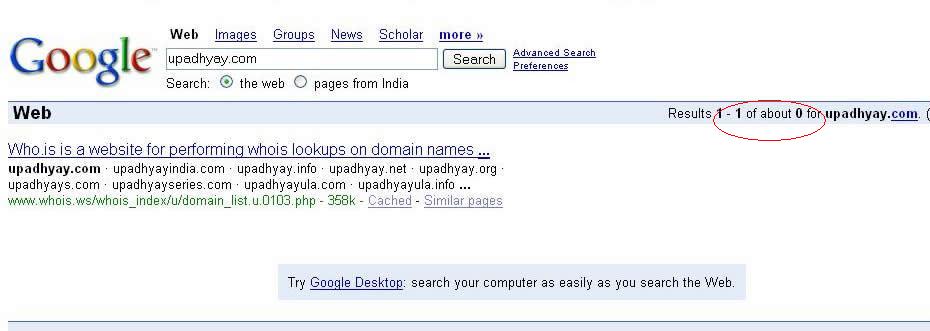
Have you ever come across a search result when Google tells you that the original number of results is pretty large, however, most of them are sort of repetitions hence they have been truncated.
Have a look at the following two pictures.
This one’s the normal result.
Here I ask Google NOT TO OMIT ANY RESULT.
You think that’s funny?
I leave it up to you to decide.
3. Slashdot, and blogs of others friends (and their friends) and some geeks like de Icauza etc. Initially I was a Digg addict, but then got completely fed up.
So guys, keep blogging. 🙂
4. Movies and Documentaries: Net speed during the night is awesome (generally). So I don’t mind downloading them. Though I don’t get time to watch them.
5. Off late I’ve also found some vulnerabilities in the policies and network of my company. I try to keep the management informed.
After all it’s my company. I’d definitely not like any jerk to poke his nose in.
That’s it.
These five (along with the songs being played ALL the time) are currently more than enough to consume my free time (In fact more than JUST the free time).
But even after all this, it gets freaking lonely sometimes… not that I am complaining 🙂